Secure Shell (SSH) is a network protocol that is used to create a secure encrypted connection between 2 computer systems. Once the connection has been established, the user can do the following tasks on the remote system
- Execute commands on the server
- X11 tunneling
- Port forwarding, and more
There are mainly 2 parties involved when creating the connection:
- SSH client
- SSH server
The SSH client creates a secure connection to the SSH server on a remote machine. So in this scenario, the user can use a SSH client in their computer and connect to a remote SSH server. There are a number of SSH clients available, both free and commercial. OpenSSH is the most widely used client in nowadays and it is available on all major platforms, including Linux, OpenBSD, Windows, and macOS.
In this Guide, We will discuss how to use the OpenSSH command-line client (SSH) to login to a remote machine and run commands or perform other operations.
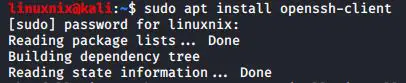
Step 01 : Installation
You have to install the openssh-client in order to connect to the remote host
#sudo apt install openssh-client
Step 02 : Connect to a remote machine using ssh with the current system login name
When the username is not given, the ssh command uses the current system login name
#ssh <hostname/ip address>
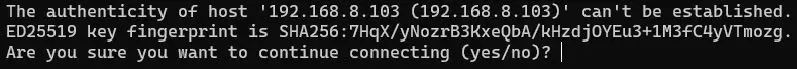
You will be prompted with a message like below when you connect to a remote machine through SSH for the first time.
Each host has a unique fingerprint and it is stored in the ~/.ssh/known_hosts file. Once you type “yes“, The fingerprint will get stored and you will be prompted to enter the password.
Step 03 : Connect to a remote machine using SSH with a different username
To log in as a different user, specify the username and the host in the following format:
#ssh <username>@<hostname>
The username can also be specified with the -l option
#ssh -l <username> <hostname>
Step 04 : Connect to a remote machine using a different port
By default, the SSH client will try to connect to the remote server on port 22. However, on some servers the default ssh port have been changed in order to add an extra layer of security to the server. You can check this article to learn more about how to secure the ssh server and reduce the attack surface.
To connect on a non-default port, use the -p option to specify the port:
#ssh -p <port_number> <username>@<hostname>
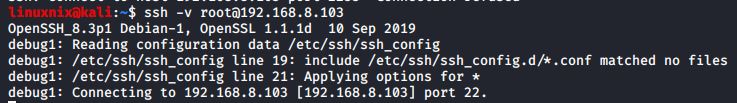
Step 05 : Troubleshoot SSH Connectivity issues
If you are experiencing authentication or connection issues, use the -v option to tell ssh to print debugging messages:
#ssh -v <username>@<hostname>
To increase the level of verbosity, you can use -vv or -vvv.
In conclusion, SSH is a great way that we can use to connect to the servers remotely when we don’t have direct physical access to the servers. For a complete list of all options, you can read the SSH man page by typing man ssh in your terminal.
Latest posts by Ruwantha Nissanka (see all)
- 4 ways to hide your identity using linux - January 18, 2021
- How To Install Kali Linux in Virtualbox - December 31, 2020
- Kali Linux : The OS That Hackers Use - December 31, 2020
- How to monitor user activity in Linux with Acct - December 30, 2020
- Debsecan : You will not miss another security update - December 28, 2020