You may have heard about firewalls before. Firewall is a security solution that can be used to monitor and control traffic that comes into and going out from our system. Iptables is the built-in firewall in a Linux machine. With Iptables, you can set rules to filter out unwanted incoming/outgoing traffic to your system. In this tutorial, let’s see how we can do that
Overview of IPTABLES
IPtables consists of four tables of rules. Each rule has its own distinct purpose
- Filter table
filter table is for basic protection of our servers and clients. this is the only table that we would normally use.
- NAT table
NAT (network address translation) table is used to connect the public Internet to private networks.
- Mangle table
Mangle table is used to alter network packets as they go through the firewall.
- Security table
Security table is only used for systems that have SELinux Installed.
Since we’re currently only interested in basic host protection, we’ll only look at the filter table. Each table consists of chains of rules and the filter table consists of the input, forward and output chains. We will first look at our current configuration using the following command
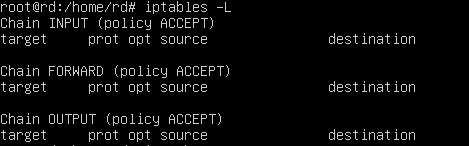
#iptables -L
we get this Output. This is associated with IPV4 and to see the configuration associated with ipv6, we will use the following command
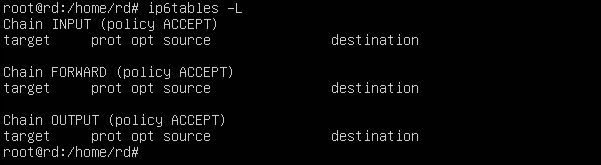
#ip6tables -L
in both cases you see that there are no rules and that the machine is wide open.
Basic Iptables Options
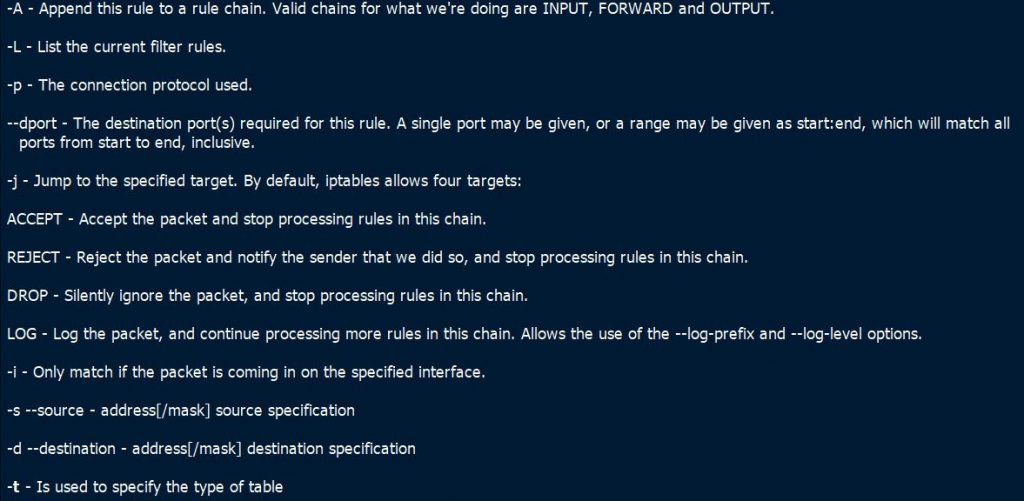
In here, I have explained some basic iptables options that you can use.
Blocking a specific IP address
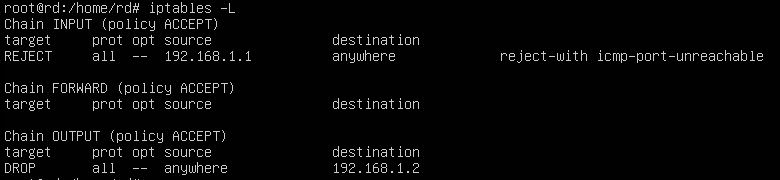
In this example, we will write a rule to block all incoming traffic from an IP address (192.168.1.1)
#iptables -t filter -A INPUT -s 192.168.1.1 -j REJECT
In this command, the option -t is used to specify the table to be used. The -A option is used to append the rule to the list of rules on the specified chain. The -s option is used to set the source IP that is to be blocked. The -j option is used tell iptables to reject the incoming traffic by using the reject target.
Block Outgoing Traffic
This is an example for block all outgoing traffic to a specific ip (192.168.1.2)
#iptables -t filter -A OUTPUT -d 192.168.1.2 -j drop
In the rule, the -d option is used to set the specify the destination IP. The -j option will drop all traffic by using the drop target.
Listing Rules
To list the rules that we have created with line numbers, you can use the following command.
#iptables -L
Deleting Rules
We can delete a rule by using -D option as shown below
#iptables -D INPUT -s 135.53.77.43 -j REJECT
Saving iptables
We now have to save the iptables rules that we have created to survive after a reboot. For that, you can use the following command.
#iptables-save
In our next tutorial, we will learn how to do Encrypting and SSH hardening.
Latest posts by Ruwantha Nissanka (see all)
- 4 ways to hide your identity using linux - January 18, 2021
- How To Install Kali Linux in Virtualbox - December 31, 2020
- Kali Linux : The OS That Hackers Use - December 31, 2020
- How to monitor user activity in Linux with Acct - December 30, 2020
- Debsecan : You will not miss another security update - December 28, 2020