Lynis is a open-source application that we can use to audit the security posture of a Linux and other UNIX-like systems. In this guide, you will learn how to install lynis and how to run a security audit on your Linux system. Lynis will give suggestions on how to fix the identified issues so it will be helpful for you to do the suggested security hardenings by yourself.
Step 1 — Installing Lynis on Your Server
Use the following command to install lynis
# apt-get install lynis
Step 2 – Performing an Audit
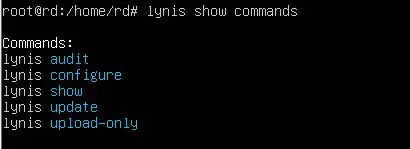
After the installation is completed, you can see the list of actions that you can perform with lynis by issuing the following command
# lynis show commands
You’ll see the following output
Execute the following command to run an audit
# lynis audit system
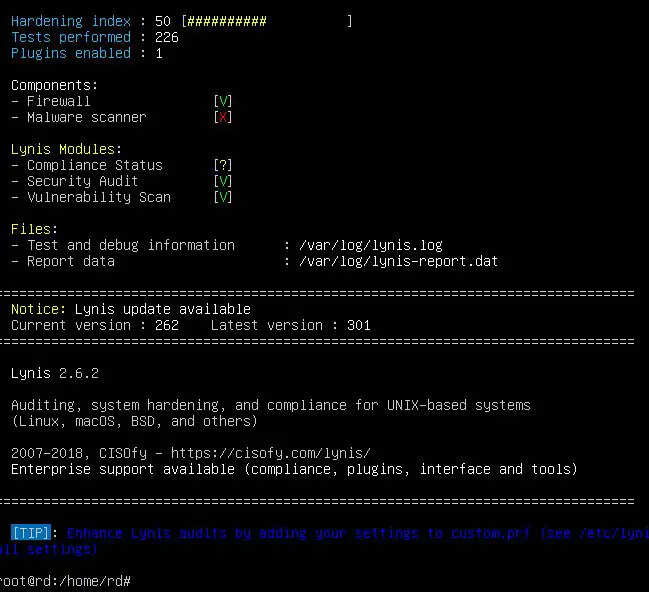
It will take a bit of time to complete the audit and once it is done, the results will be shown as follows
When Lynis performs an audit, it goes through a number of tests, divided into categories. After each audit, test results, debug information, and suggestions for hardening the system are written to standard output (the screen). More detailed information is logged to /var/log/lynis.log , while report data is saved to /var/log/lynis-report.dat
The report data contains general information about the server and the application itself, so the file you’ll need to pay attention to is the log file. The log file is purged (overwritten) on each audit, so results from a previous audit are not saved.
Once the audit is complete, you’ll review the results, warnings, and suggestions, and then implement any of the relevant suggestions. The results you see on your audit may be different, but you should still be able to follow along.
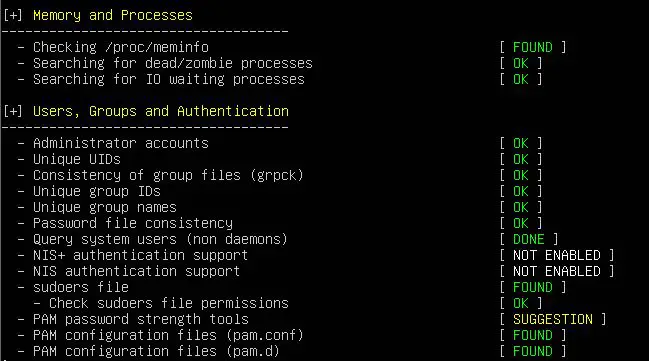
The significant part of a Lynis audit output is purely informational. It tells you the result of every test, grouped by category. The information takes the form of keywords, like NONE, WEAK, DONE, FOUND, NOT_FOUND, OK, and WARNING.
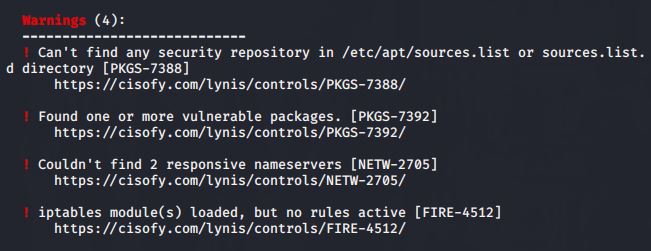
Warnings are listed after the results section. Each warning starts with the warning text itself, with the test that generated the warning on the same line in brackets.
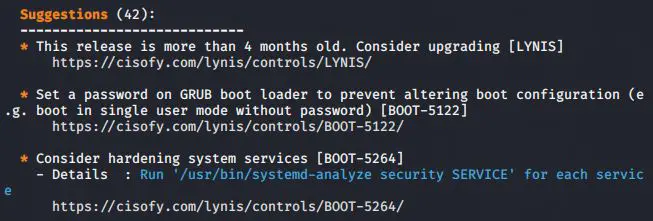
After the warnings section, you’ll see a series of suggestions that, if implemented, can make your server less vulnerable to attacks and malware.
With these results, now you can fix the remaining security issues on your system and make it more secure from the attackers.
Latest posts by Ruwantha Nissanka (see all)
- 4 ways to hide your identity using linux - January 18, 2021
- How To Install Kali Linux in Virtualbox - December 31, 2020
- Kali Linux : The OS That Hackers Use - December 31, 2020
- How to monitor user activity in Linux with Acct - December 30, 2020
- Debsecan : You will not miss another security update - December 28, 2020