DIG command explained with examples in Linux
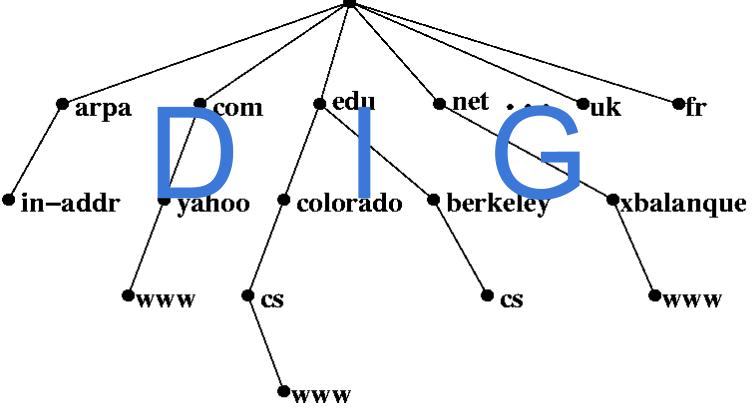
In this post I am going to teach How to use DIG and with examples. DIG is one of the most important tool in debugging DNS server related issues. Some points to be noted about DIG. 1.DIG full-form/abbreviation is Domain Information Groper 2.DIG can work on command line or as well in batch mode 3.DIG supports Internationalized Domain Name(IDN) convections too. 4.DIG is more advanced than older tools such as nslookup and host commands. 5.DIG output have so much information than any other tool, such as Question/Answer/Authority sections (which we are going to discuses in this post) Usage1 : Using...
Read More